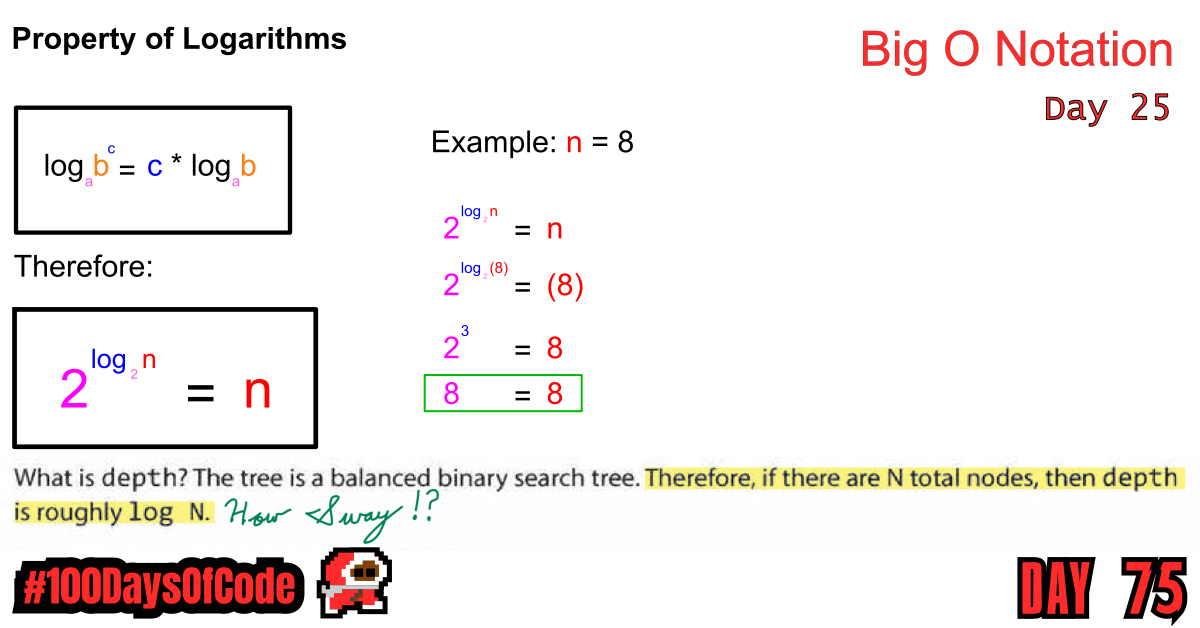
It seems like I have found another rabbit hole to jump down. Example 9 used a “Balanced Binary Search Tree” as an example and it has me asking a lot of questions. The book nonchalantly mentions how we can roughly calculate the depth of a Balanced binary search tree with N nodes with log (N). It does not elaborate on that solution so I had to start digging. It feels like this might take me on a long journey. I hope not but you never know.
TLDR;
Okay, so here are the highlights of what I did:
- Still reading through the book “Cracking the Coding Interview” by Gayle Laakmann McDowell. Still working on example nine. I looked into how she calculated the depth of any balanced binary search tree only to realize how little I remembered about the terminology surrounding binary search trees in general. It seems like I need to review those as well before I can answer my original question on calculating depth.
- Continued working through the module called “Introduction to Microsoft Power Platform”. I read through a section discussing data loss prevention, privacy, and accessibility. Reading this section made me realize how much I want to learn more about networking and how secure internet connections can be as well as how weak they can get.
Conclusion
That’s all for today. If you are interested in the MIT course you can check out the video lecture I’m currently going through. The lecture is helpful but isn’t sufficient by itself. Anyways, until next time PEACE!